NetSkateKoban Nano(V)
NetSkateKoban Nano(V) is a product that responds to the need to “build security functions (detection and connection blocking of unauthorised terminals) to protect information systems from the threat of unauthorised terminals without any hassle”. In addition to the functions of NetSkateKoban Nano, networks configured with VLANs (Virtual LANs) are supported.
NetSkateKoban's powerful security features are retained, but can be easily implemented without the need for specialist knowledge.
Flexible support for small networks to large networks spanning multiple locations.
Note: The product for networks with physically segmented configurations is NetSkateKoban Nano.
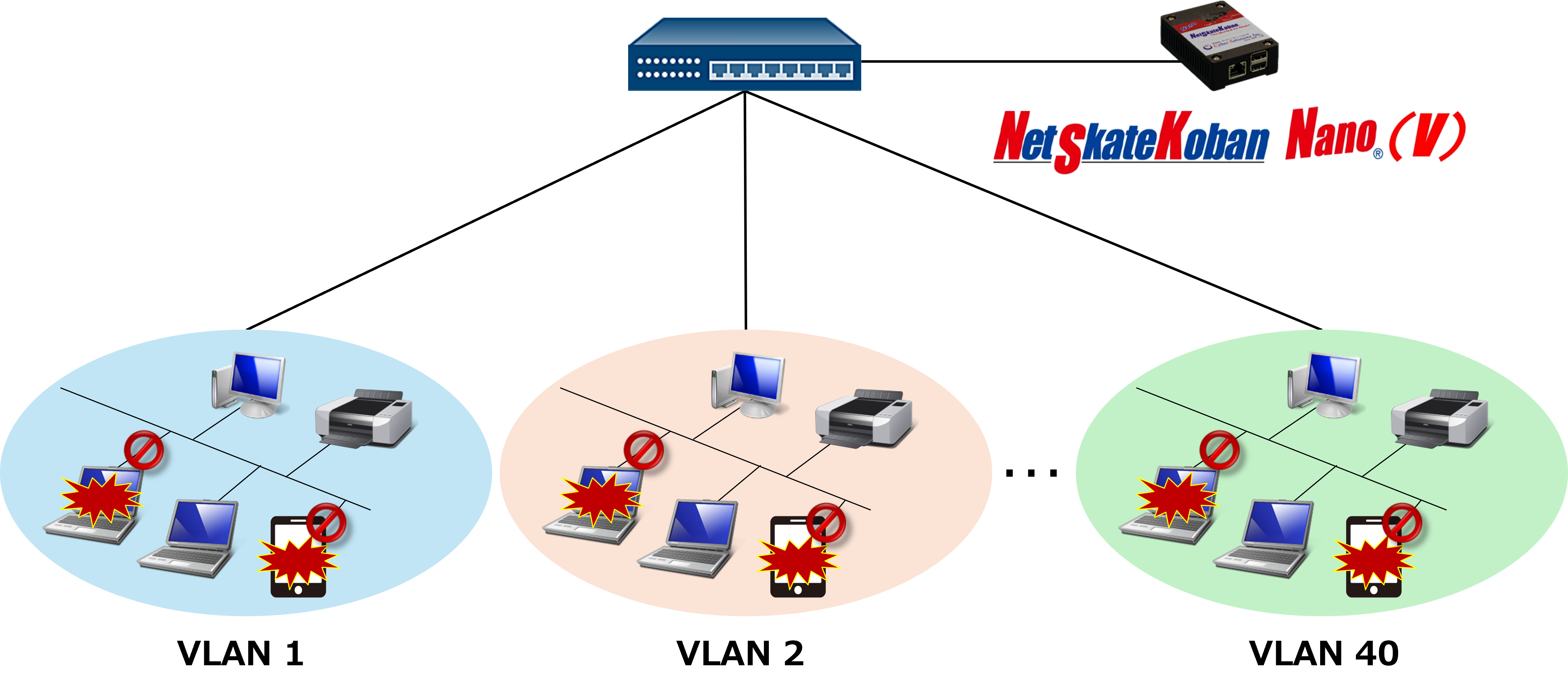
One Nano(V) can monitor up to 40 VLANs
Case study
GIGA School Concept
NetSkateKoban Nano(V) is perfect for the GIGA school concept that is being promoted under the Society 5.0!
We have prepared an optimal solution that meets the security requirements of GIGA School.
We are also able to offer added value proposals regarding security to system integrators who are proposing network equipment.
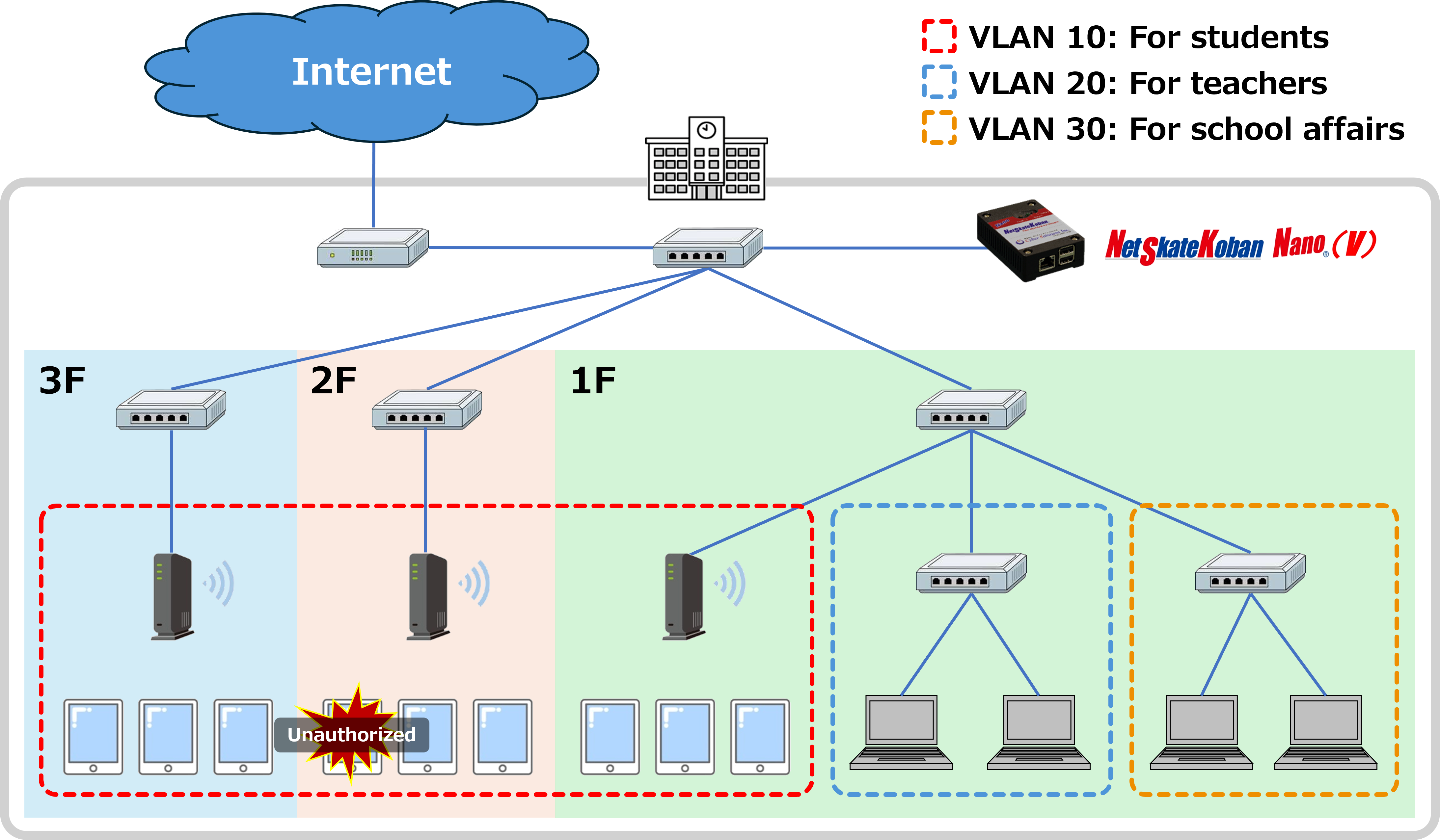
Initiatives for the GIGA School Concept

Why choose NetSkateKoban Nano(V)?

GIGA School Concept Requirements
In order to build and operate the GIGA School Concept network efficiently and safely, the following requirements must be met.
- Want to manage/monitor without knowing IT in detail
- Want to centrally manage multiple school affairs/learning networks
- Want to centrally manage multiple schools
- Want to centrally monitor regardless of wired or wireless environment
- Want to monitor the connection status of my PC/smartphone
- Want to prohibit unauthorized network connections
- Want to block terminals (wireless APs) that connect without permission
- Want to stop connections at night/holidays for each terminal
- Want to make installation easy
- Want to perform simple terminal authentication
- Want to cooperate with existing UTM/antivirus software
- Want to consider security measures with an eye to the future
- Want to centrally manage/monitor without depending on network configuration
- Want to spend as little money as possible
NetSkateKoban Nano(V) Introduction Pattern
By connecting Nano(V) to the core switch, all networks can be monitored.
Features and Functions
In addition to the features and functions of NetSkateKoban Nano, it supports networks configured with VLANs.
No specialist knowledge is required, from installation to operation.
Features
- A network configured by VLAN can be monitored with a single Nano(V) terminal.
- No management server, terminal agent, or terminal license is required; it can be used with just a browser.
- Collectively monitor and control wireless and wired terminal connections.
- Although it is small, it has advanced detection and blocking functions.
- If an unregistered terminal is detected, the administrator will be notified by email.
- Identifies and displays the vendor name and OS name of the detected terminal.
- Detected terminals can be added to Allowed Terminal List (list of terminals allowed to connect) with one touch.
Functions
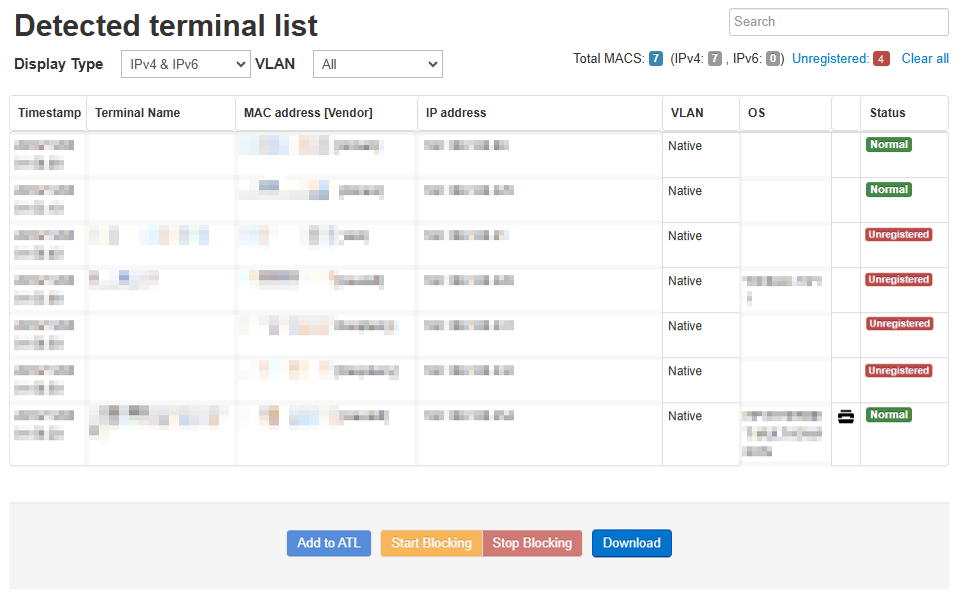
Terminals Detection/Display
- Display a list of connected terminals
- Display a list of blocked terminals
- Auto Active Detection (Detect terminals that do not actively communicate over the network, such as Wi-Fi routers, Ethernet switches, printers, and IoT terminals.)
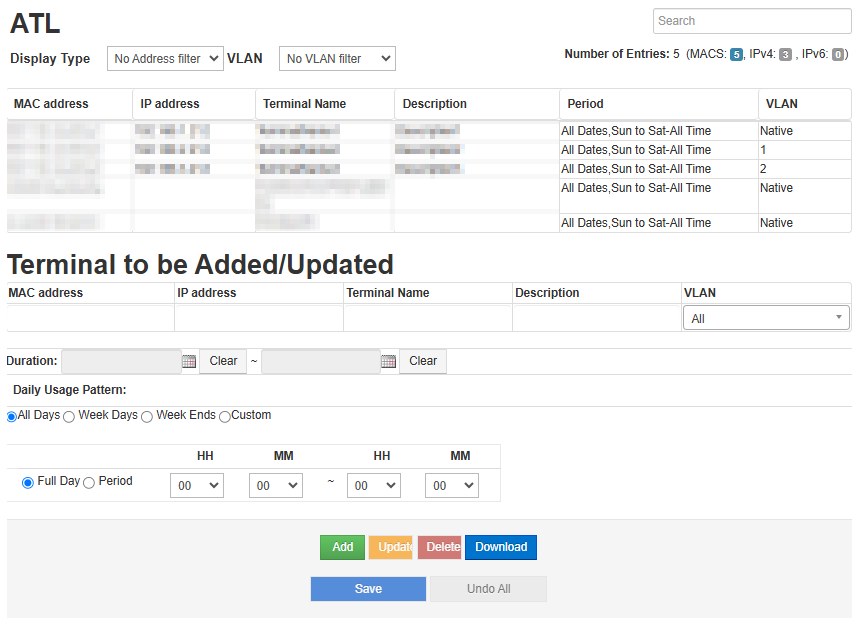
Allowed Terminal List (ATL) Management
- Manual registration of Allowed Terminal List (you can also register from Detected Terminal List)
- Allowed Terminal List (ATL) file upload/download
- Setting the period (date, day of the week, time) during which terminal connections are allowed
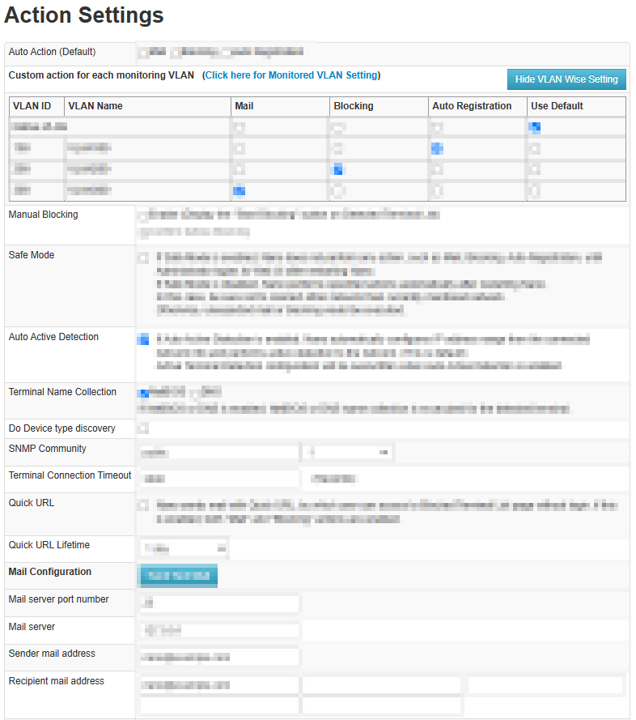
Action settings when unregistered terminal is detected
- Multilateral Communication Interference
- Email notification
- Auto Registration to Allowed Terminal List (ATL)
- Quick URL
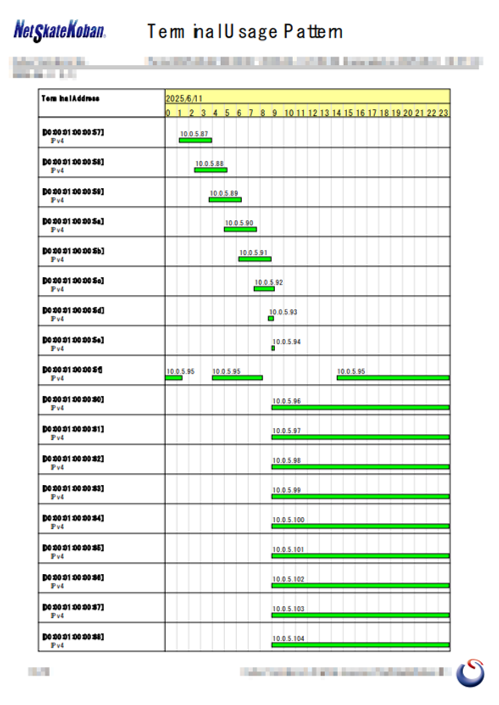
Report Output
- Weekly report of Terminal Usage Pattern
Peer List
You can check the information of communication between a specific terminal and other terminals in the vicinity (peer-to-peer communication) in a list.
Peer List information allows you to check "when" and "with which terminal" the communication occurred.
In the event of infection by a computer virus or ransomware, using Peer List function can help prevent the spread of secondary damage.
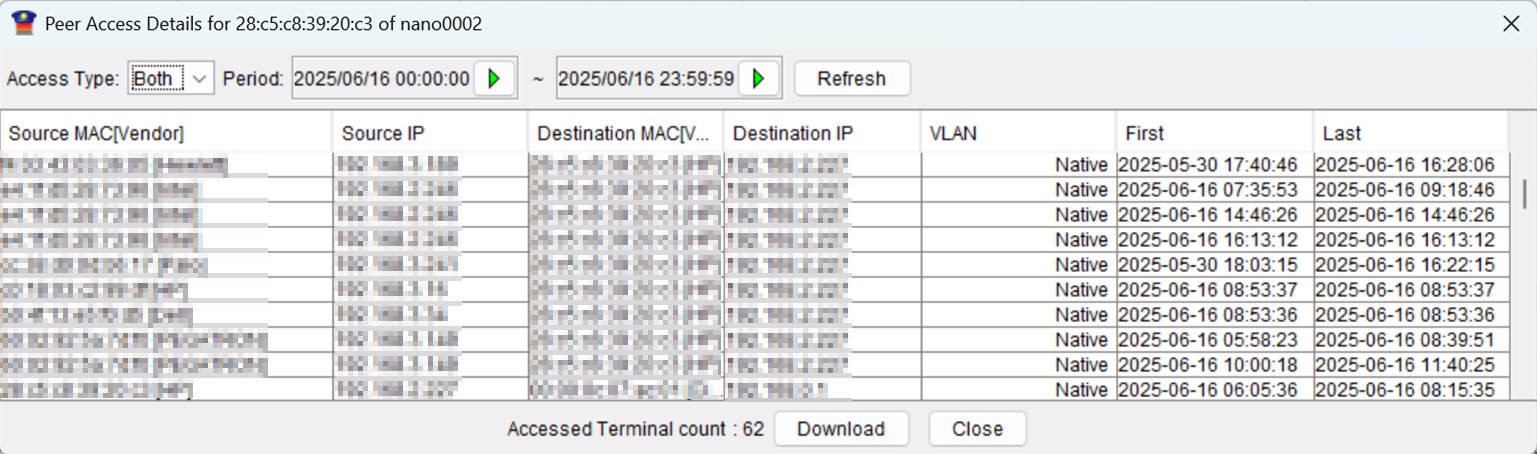
Note: The use of Peer List requires the combination of Nano Manager.
SNMP Traps and Syslogs sent from anti-virus products and UTM (Unified Threat Management)s can be used to acquire terminal information, identify terminals and link to functions such as blocking and email notification. This function can be used to deter the spread of computer viruses and other infections and provide a multi-layer defence.
| Vendor Name | Types of SNMP Trap and Syslog |
|---|---|
| Fortinet | IPS, Anomaly Detection, Virus Detection, Web Filtering, DNS Filtering, Botnet, Sandbox |
| SonicWall | Content Filter, Gateway Antivirus Service, Intrusion Prevention System, Botnet |
| Trellix (Former Company FireEye) | Notification |
| Trend Micro | Virus Detection, Virus Infection |
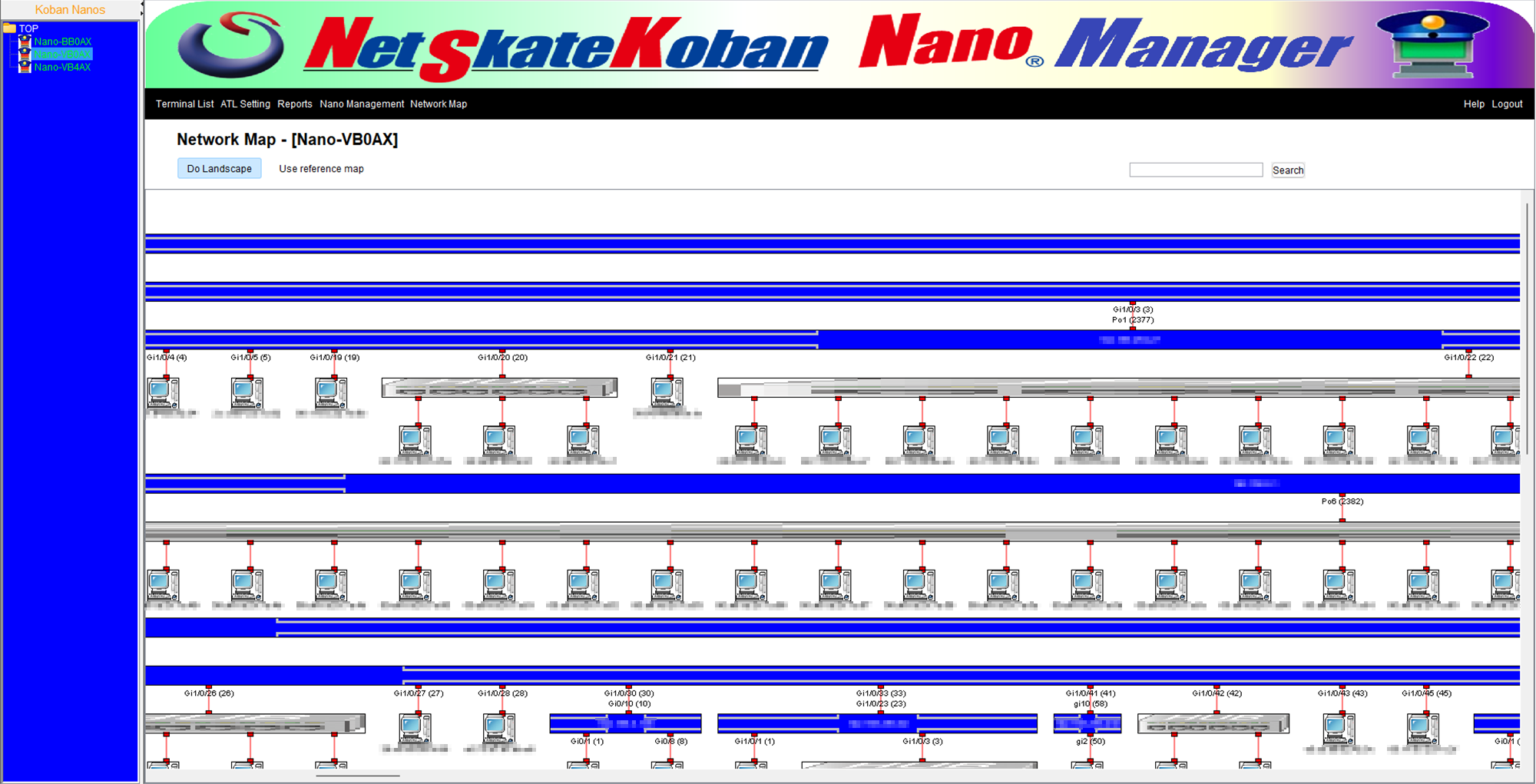
Network Map
- By automatically analyzing the connection relationships of each terminal and switch, a network map is generated.
- The terminal icon on the network map shows the information detected by NetSkateKoban Nano(V).
- The generated network map can be edited later.
- The network map can be output in image file format.
Note: The use of Network Map requires the combination of Nano Manager.
Specification
Functional Specifications
| Terminal detection | ARP detection |
| Terminal management | Allowed Terminal List (ATL) registration system (all day permission/time zone specified permission) |
| Blocking method | Multilateral communication interference (patented technology) |
| Notification | Send alert email |
| Monitoring interface | Web UI operation (list display, CSV output) |
| Setting interface | Web UI operation, CSV import supported (same for manager for unified management of multiple terminals) |
Hardware Specifications
| External dimensions | Approximately 24.3(H) x 83(W) x 58(D) mm (excluding protrusions) |
| Weight | 80 [g] (main body), 105 [g] (AC adapter) |
| LAN interface | 10BASE-T / 100BASE-TX (AUTO-MDIX compatible) x 1 port |
| Operating temperature range | -20 ~ 70℃ |
| Power supply | 100 – 240V (AC adapter included) |
| Power consumption | Typ. 1.2W |
